Sidebar
Table of Contents
28.2.5 GPG - Digression
An alternative to the methods described for protecting the contents of a file with a password is to encrypt a file with a GnuPG public key. This alternative is useful if you frequently have to encrypt files - for example, backup files of databases - or directory archives or emails. In this case, it is worthwhile to create a key pair of private and public keys with GnuPG, because the gnupg programme package is pre-installed in all current Ubuntu versions, for example. A look at the programme help is indispensable before you work with the GnuPG (gpg) programme for the first time:
hans@linux:~$ gpg –help
You can easily create a new key pair consisting of private and corresponding public key in the terminal, because you will be guided through the entire process:
hans@linux:~$ gpg --gen-key gpg (GnuPG) 1.4.11; Copyright (C) 2010 Free Software Foundation, Inc. ... Please select which type of key you would like: (1) RSA and RSA (default). (2) DSA and Elgamal (3) DSA (sign/authenticate only) (4) RSA (sign/authenticate only) Your choice? 1 RSA keys can be between 1024 and 4096 bits long. Which key length do you want? (2048) ...
28.2.5.1 Program 'Seahorse'
At http://wiki.ubuntuusers.de/Seahorse you will find a good description of how to use the graphical frontend for the encryption programme 'GnuPG', with the first part focusing only on the generation of a key pair. You start the Seahorse programme via Applications | Accessories | Passwords and Encryption or by calling the command 'seahorse' in a console. Follow the individual forms after starting with File> New. Select the entry type and enter the required entries:
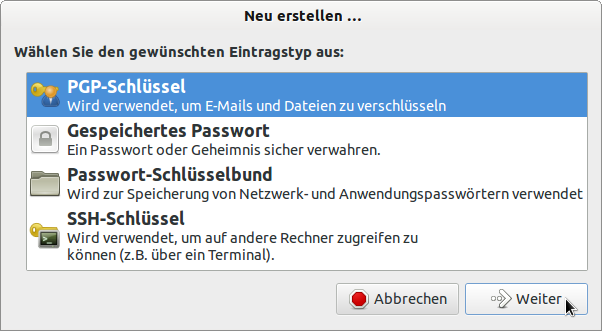
Figure 28.2.5.1.1: Selecting the entry type
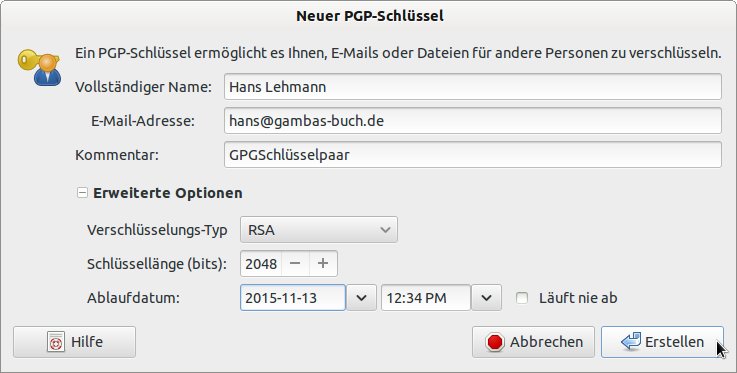
Figure 28.2.5.1.2: Entering the key data
- An expiry date should be set.
- The option of “Never expires” should be avoided.
- After confirming 'Create', a key (pair) is created.
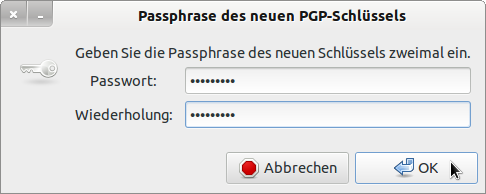
Figure 28.2.5.1.3: Entering the private key
Finally, Export writes the public key to a text file with the extension .asc, which is saved in the home directory. The suggested file name should be changed so that it does not contain any spaces: hans_lehmann.asc or hans.lehmann.asc.
Under Properties you can view more details about the generated public key.
28.2.5.2 Using the generated key pair
- The public key is sent to a person who can encrypt a file, archive or email with this key or it is deposited on a key server.
- The content of files protected with a public key can only be read by the person who has the private key of the key pair.
28.2.5.3 Encrypting a single file
Initial situation:
- The persons E and S arrange that S sends to E selected files, which S encrypts beforehand with E's public key.
- Person E sends to person S the public key of a GPG key pair.
- S imports the public key - for example with the help of the programme 'seahorse' and thus knows exactly the information to encrypt a selected file with E's public key.
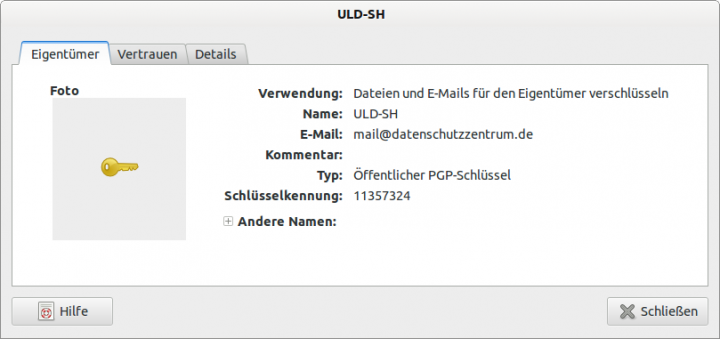
Figure 28.2.5.3.1: Entering the private key
For encryption, a public key of the author is used for the demonstration because then decryption with the private key belonging to the key pair can also be shown quickly:
Command in a console:
hans@linux:~$ gpg --encrypt -a --recipient hans@gambas-buch.de /home/hans/DBT/daten.csv hans@linux:~$ gpg --encrypt --armor --recipient E06BA316 /home/hans/DBT/daten.csv
The specification of the email address already contains the reference to the (own) public key, which is part of the public key! However, you can also enter the key identifier directly. The file to be encrypted is data.csv. The content of the generated encrypted file is in readable ASCII (Armor) format in the file data.csv.asc.
28.2.5.4 Decrypting a single file
To decrypt the file data.csv.asc, the author's private key is needed and only one person has it - the author!
After executing the following command in a console, one is prompted to enter the private key (passphrase):
SYNTAX: hans@linux:~$ gpg --decrypt --output 'Destination file path' 'Source file path'.
hans@linux:~$ gpg --decrypt --output /home/hans/DBT/daten.csv /home/hans/DBT/daten.csv.asc
You need a passphrase to unlock the secret key.
User: "Hans Lehmann (GPG key pair) <hans@gambas-buch.de>"
2048-bit RSA key, ID DE7B82D4, generated 2014-11-13 (master key ID E06BA316).
gpg: encrypted with 2048-bit RSA key, ID DE7B82D4, generated 2014-11-13.
"Hans Lehmann (gpg key pair) <hans@gambas-buch.de>"
hans@linux:~$
Figure 28.2.5.4.1: Entering the private key
Afterwards, the original file can be found at /home/hans/DBT/data.csv.
28.2.5.5 Example 2
Encrypting a file with the public key:
hans@linux:~$ gpg --encrypt -a --recipient wer@ist.da /home/hans/DBT2/daten.csv
At the recipient's end, the file is decrypted with the private key and the decrypted file is saved in a text file with a different file name → data_backup.csv:
Syntax: gpg --decrypt --output Destination Source
hans@linux:~$ gpg --decrypt --output /home/hans/DBT2/daten_backup.csv /home/hans/DBT2/daten.csv.asc
You need a password set to unlock the secret key
for user: "Hans Lehmann (data security) <wer@ist.da>" to unlock the secret key
2048-bit ELG-E key, ID 99028A2D, created 2010-08-19 (master key ID 44337DE4)
gpg: encrypted with 2048-bit ELG-E key, ID 99028A2D, created 2010-08-19
"Hans Lehmann (data security) <wer@ist.da>"
hans@linux:~$
This is what the (readable) content of a public key looks like:
-----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v1.4.11 (GNU/Linux) mQENBFRkmCUBCADAJ1ZDmTPLdnLdRGcJtPfuPjZJKq/33ESaY/adGy4m2xGmsDeh QrNGjqpK2WV5izHQxiUkECacjPqsgG7Y4DysKCbV4TB/gu3fWNNdLnIaaUYkDzqN gSavC3HKqRM4Z0rth5U0nX2CAaTZ8fuRaOcHSne+ZKWQ3xuvMt+C0vZ7ANSZLTz3 2PtpNDQO1KagDC9KDDBUNbXXgpcpylK0PFRldlf/4Haf5aenLvHmLeZM+1AXjI90 Q/yvq5siZTkj3fHcgsnvMylq1eO+Vb+basMAcAVsma//XjiNaTrd8xqx3ssLDf/b fl55r6i4QcNM1eMns8hcLHQMnVDAK+WA166NABEBAAG0NkhhbnMgTGVobWFubiAo ... 3M+TnKcuPV1TpNBkWwhlmdsLpt0lBQznhwCo5AHZQ03Kl3he9y/xRW303uYR7BAN Amyw2wlG2PCu7yDrXQ7icpjkyqLrJ1j3SeF7GIvZNGhq5AHqmFaGikoRMvulqSa4 ZtJ8bH2cYTrKP0T5kjoYEuEkHVvD2KollobmFtaGlwEe/x0vI/ZHDGwGmEqcrdAv H4JNO0kkntWZYGTIDcK6x5Q= =BolE -----END PGP PUBLIC KEY BLOCK-----

