Sidebar
Table of Contents
24.14 Digression: SSH server/SSH client - installation, configuration and testing
If you value the following features in a TCP/IP connection from your computer to a remote computer:
- Authentication of the remote terminal,
- encryption of the data transmission and
- data integrity,
then it is worth installing an SSH server on the remote computer. The SSH protocol enables encrypted connection of computers and execution of terminal commands on the remote computer.
24.14.1 Notes
The following notes and suggestions should be followed:
- This description describes how to install the OpenSSH server - the free implementation of 'Secure Shell'.
- An SSH client is automatically installed by all Linux distributions during installation!
- For many administrative tasks and tests, the OpenSSH client `ssh` is used in a console.
- Reference is only made to the OpenSSH server documentation.
Encrypted terminal connections are particularly useful when a server has been set up 'headless' - i.e. without keyboard, screen or graphical user interface. The procedure described in this excursus is only suitable for use within a home network.
24.14.2 Installing OpenSSH client
This allows you to determine which OpenSSH packages are already installed on the remote computer. An output might look like this:
hans@mint20:~$ dpkg --list | grep openssh ii openssh-client 1:8.2p1-4ubuntu0.3 amd64 secure shell (SSH) client, for secure access to remote machines hans@mint20:~$
Good - an SSH client is already installed on this system, which is the standard on Linux mentioned earlier. Otherwise, an SSH client is quickly installed:
$ sudo apt-get update $ sudo apt-get upgrade $ sudo apt-get install openssh-client
24.14.3 Installing OpenSSH server
An OpenSSH server is not installed by default on Ubuntu and Mint. It can be installed via the application management or you can enter the following lines one after the other in a terminal:
$ sudo apt-get update $ sudo apt-get upgrade $ sudo apt-get install openssh-server
24.14.4 Controlling the OpenSSH server
Attention.
The SSH server is automatically started at every system start (default). You can change this with these two commands:
$ sudo systemctl disable openssh -- OpenSSH aus der Autostart-Liste entfernen $ sudo systemctl enable openssh -- OpenSSH der Autostart-Liste wieder hinzufügen
If the SSH server is not allowed at system start-up, then you can start it yourself.
The following calls in a terminal control the SSH server with the parameters in the list:
$ sudo systemctl parameter ssh {start|stop|reload|force-reload|restart|try-restart|status}
$ sudo service ssh parameter {start|stop|reload|force-reload|restart|try-restart|status}
Examples:
$ sudo service ssh stop $ sudo systemctl stop ssh -- Alternativ bei einem ubuntu-basierten System
The SSH server service should already be active after the installation is complete. Here's how to check:
$ service ssh status -- Nur bei der Statusabfrage ohne erhöhte Berechtigung
● ssh.service - OpenBSD Secure Shell server
Loaded: loaded (/lib/systemd/system/ssh.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2021-11-29 15:28:49 CET; 2h 56min ago
Docs: man:sshd(8)
man:sshd_config(5)
Process: 682 ExecStartPre=/usr/sbin/sshd -t (code=exited, status=0/SUCCESS)
Main PID: 733 (sshd)
Tasks: 1 (limit: 18939)
Memory: 3.2M
CGroup: /system.slice/ssh.service
└─733 sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
Nov 29 15:28:49 pc-mint20 systemd[1]: Starting OpenBSD Secure Shell server...
Nov 29 15:28:49 pc-mint20 sshd[733]: Server listening on 0.0.0.0 port 22.
Nov 29 15:28:49 pc-mint20 sshd[733]: Server listening on :: port 22.
Nov 29 15:28:49 pc-mint20 systemd[1]: Started OpenBSD Secure Shell server.
24.14.5 Documentation
Extensive documentation on OpenSSH can be found at:
https://www.openssh.com/manual.html
24.14.6 Log files
Log entries of the OpenSSH server can be found in the file /var/log/auth.log. Here is an excerpt:
Nov 21 10:36:46 mint20 sshd[7016]: Server listening on 0.0.0.0 port 22. Nov 21 10:36:46 mint20 sshd[7016]: Server listening on :: port 22.
24.14.7 Connection data
If you want to establish an SSH connection from your computer with an SSH client to a remote computer with an SSH server, then you need the following data:
- IP address of the SSH server host or, in a DHCP environment with a DNS server, its host name and.
- the account data (name, password) of a system user on the SSH server host or
- a key pair consisting of a public and a private key (option).
Use the following commands to determine the IPv4 address and the IPv6 addresses on the SSH server host or SSH client host.
hans@pc-mint20:~$ hostname -I | grep -oE '([[:digit:]]{1,3}\.){3}[[:digit:]]{1,3}' # IPv4
192.168.0.2
hans@pc-mint20:~$ hostname -I | grep -oE '([a-fA-F0-9]{1,4}\:){7}[a-fA-F0-9]{1,4}' # IPv6
2a02:8109:b8bf:f2ec:2010:2d22:8ecb:31d0
2a02:8109:b8bf:f2ec:e101:fa83:9d1:7b1c
2a02:8109:b8bf:f2ec:bfb0:6aab:b6f5:f9ea
You can get an overview of all IP addresses and host names in your (home) network by taking a look at the network configuration of your router.
24.14.8 SSH connection with password authentication
A connection to the SSH server can be established with something like the following command, using the IP address of the server and a system user name on it - here `hans`:
honsek@laptop-mint20:~$ ssh hans@192.168.0.2 The authenticity of host '192.168.0.2 (192.168.0.2)' can't be established. ECDSA key fingerprint is SHA256:HqdkscKY8DwNMCqw3Xj2ga5pWQ3VyGpD5rzLttRLLsQ. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
At the very first login, the fingerprint of the public key of the SSH server is displayed - here as a SHA-256 hash of the public ECDSA key marked in blue. If the remote computer with the SSH server is in your home network, you can dispense with checking the fingerprint in this case and continue the dialogue with 'yes'. You will then be prompted to enter the system user password on the remote computer:
honsek@laptop-mint20:~$ ssh 192.168.0.2 The authenticity of host '192.168.0.2 (192.168.0.2)' can't be established. ECDSA key fingerprint is SHA256:HqdkscKY8DwNMCqw3Xj2ga5pWQ3VyGpD5rzLttRLLsQ. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.0.2' (ECDSA) to the list of known hosts. hans@192.168.0.2's password: hans@pc-mint20:~$
Note the last line - you will see the prompt of the server!
By entering the user name in hans@192.168.0.2 and the password, you have proven your identity, which the SSH server checks using the account data known to it (user name, password) and then grants access to the secured area. This establishes an SSH connection between the SSH server and the SSH client.
You can now administer the SSH server as if you had opened a console there. This is tested immediately by executing a find command on the remote computer as an example:
hans@pc-mint20:~$ find /etc/ssh -type f -name '*conf*' /etc/ssh/ssh_config /etc/ssh/sshd_config /etc/ssh/sshd_config.d/sshd.conf hans@pc-mint20:~$ exit Abgemeldet Connection to 192.168.0.2 closed. honsek@laptop-mint20:~$
To terminate the SSH connection, enter `exit` and you are then back in the console on the SSH client host. For all further connection attempts from the same client, the SSH server waives warnings because the client registers the host as known in the file ~/.ssh/known_hosts during the first SSH connection.
Since in a home network one is often dealing with a DHCP environment in which IP addresses can change, it is a good idea to use the host name as an alternative to the IP address for a login on the remote computer. A login with the host name then looks like this, for example:
honsek@laptop-mint20:~$ ssh hans@pc-mint20
24.14.9 Checking the SSH server fingerprint
If you are in a different location or network domain with the SSH client host, then for security and before establishing the first SSH connection, you should take a checking look at the fingerprint of the SSH server's public key. This is the only way to ensure that you are connecting to the correct SSH server.
You can determine the fingerprint of the public server key locally and directly on the SSH server host with the following console command:
hans@pc-mint20:~$ ssh-keygen -l -f /etc/ssh/ssh_host_ecdsa_key.pub 256 SHA256:HqdkscKY8DwNMCqw3Xj2ga5pWQ3VyGpD5rzLttRLLsQ root@mint20 (ECDSA) hans@pc-mint20:~$
If there is no direct local access to the SSH server host, connect locally via an SSH connection as described above and make a note of the displayed fingerprint in case of an initial connection or enter the above console command in a console on the client.
SSH connections via the Internet can also be operated with a high level of security, but the setup is critical and also includes the firewall. A description of this variant is omitted here.
24.14.10 SSH connection with public key authentication
As an alternative to SSH connection with password authentication, one can also set up the server and client to connect without entering a password. This is generally considered to be the more secure form and is achieved by publicising public keys or public keys and making appropriate configurations. The following section builds on the SSH server and SSH client setups described above and uses the capabilities acquired with them.
24.14.10.1 Creating a key pair (private key and public key)
To be able to prove your identity to the SSH server, first generate a key pair on the SSH client. Choose a suitable passphrase in the dialogue, which you must remember! This ensures that the generated keys are stored in encrypted form.
honsek@laptop-mint20:~$ ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/hans/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/hans/.ssh/id_rsa Your public key has been saved in /home/hans/.ssh/id_rsa.pub The key fingerprint is: SHA256:/ouoLhznowzUXi6tMeMhR0uv3h4XsEz3LYVc2y+2Oxg honsek@laptop-mint20 The key's randomart image is: +---[RSA 3072]----+ | . | | . o o | | o . o o . | | . o + . o . | | . + + .So . o . | |. = B .. .E. o | |.o & = .. o. | | o* % o. o . .. | | +O+=. . o. .. | +----[SHA256]-----+ honsek@laptop-mint20:~$
Then restrict access to the private key to the current system user:
honsek@laptop-mint20:~$ chmod 700 .ssh/id_rsa
24.14.10.2 Adjusting the SSH server configuration
Establish an SSH connection via password authentication to the SSH server and start the editor `sudo nano /etc/ssh/sshd_config` there in the console with elevated rights with the configuration file as parameter.
Check with
sudo nano /etc/ssh/sshd_config
whether the configuration file /etc/ssh/sshd_config contains the line
PubkeyAuthentication yes
is without a leading #. If not, change this line. After saving the changed SSH server configuration, do not forget to restart the SSH server. Close the existing SSH connection.
honsek@laptop-mint20:~$ ssh hans@192.168.0.2 hans@192.168.0.2's password: Last login: Tue Nov 30 17:56:50 2021 from 192.168.0.3 hans@pc-mint20:~$ sudo nano /etc/ssh/sshd_config hans@pc-mint20:~$ sudo service ssh restart hans@pc-mint20:~$ exit honsek@laptop-mint20:~$
24.14.10.3 Transferring the public key to the SSH server
To copy the public key from your SSH client host to the SSH server in the specified hidden directory:
honsek@laptop-mint20:~$ ssh-copy-id -i ~/.ssh/id_rsa.pub hans@192.168.0.2 /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/hans/.ssh/id_rsa.pub" /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys hans@192.168.0.2's password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'hans@192.168.0.2'" and check to make sure that only the key(s) you wanted were added. honsek@laptop-mint20:~$
After entering the password of the system user, a window will pop up. Here you must enter the passphrase that you had set when creating the key pair. You can also specify whether the password should be permanently unlocked. We implement the request to connect to the SSH server on a test basis now:
honsek@laptop-mint20:~$ ssh hans@192.168.0.2 Last login: Tue Nov 30 17:56:50 2021 from 192.168.0.3 hans@pc-mint20:~$ exit Abgemeldet Connection to 192.168.0.2 closed. honsek@laptop-mint20:~$
As you will notice, a password is no longer required to prove your identity on the server, as the stored key is now used.
24.14.11 Adjusting the SSH client configuration
On your computer, create the configuration file config
$ sudo xed ~/.ssh/config
and enter the following exemplary content. Lines beginning with a '#' are disabled. As you will notice, it is possible to configure multiple hosts. Note the bold line where you can specify any identifier for the host. This can be used as a proxy when establishing a connection. Only in a DHCP environment may the host name be entered in the 'HostName' parameter instead of the IP address. If fixed IP addresses are used, the IP address must be entered there!
# 2021-11-20 # # Aus c't 2018, Heft 14, S. 144 ff # Inhalt von 'config' in ~/.ssh # Host h150 HostName pc-mint20 Port 22 User claus IdentityFile ~/.ssh/id_rsa # #Other Hosts #Host ems # HostName 192.168.1.10 # Port 22 # User pi # IdentityFile ~/.ssh/id_rsa # #Host NAS # HostName 192.168.1.2 # Port 22 # User admin # IdentityFile ~/.ssh/id_rsa 24.14.11.1 Test
In future, your login should succeed with this command in a console:
$ ssh h150
Alternatively, you can still use the familiar syntax, but you will no longer be asked for a password:
$ ssh hans@192.168.0.2 $ ssh hans@pc-mint20
24.14.12 Extension - file transfer
The SSH protocol, for example, not only ensures secure transmission of account data (user name, password), but also more secure data transmission. The console programme for secure file transfer from one system to a remote target system via SSH is called `scp` (SecureCopy) and is executed on the SSH server.
It uses the following syntax to securely copy a file:
$ scp client-pfad-zur-orginal-datei [ziel-user-name]@[ziel-ip/hostname]:pfad-auf-dem-entfernten-ziel-system
In the following example, as system user `honsek` from the SSH client host with the hostname `laptop-mint20`, you copy the text file `~/desk/remote_via_scp.txt` to a remote target system with the IP address `192.168.0.2` in its (home) directory `/home/hans`.
honsek@laptop-mint20:~$ scp /home/honsek/Schreibtisch/fernzugriff_via_scp.txt hans@192.168.0.2:/home/hans fernzugriff_via_scp.txt 100% 2131 517.2KB/s 00:00 honsek@laptop-mint20:~$
With public-key authentication fully set up, this also succeeds with:
honsek@laptop-mint20:~$ scp /home/honsek/Schreibtisch/fernzugriff_via_scp.txt h150:/home/hans fernzugriff_via_scp.txt 100% 2131 517.2KB/s 00:00 honsek@laptop-mint20:~$
Secure copying only works if you also have an account on the SSH server, as the password of the system user is requested there, or without a password if public key authentication has been set up.
Alternative 1
With this destination entry in the file manager `nemo` of Linux Mint
ssh://192.168.0.2/home/hans/dbt sftp://192.168.0.2/home/hans/dbt
you establish a secure FTP connection (SFTP) to an SSH server with the address `192.168.0.2` and see the contents of the directory `/home/hans/dbt`. Now you can select a file there, copy it and place it in your own home directory in a selected directory or vice versa.
Alternative 2
Start the following dialogue in the file manager under 'File/Connect to Server' and enter all relevant data, whereby you can enter its IP address, host name or the alias name from the file ~/.ssh/config for 'Server:':
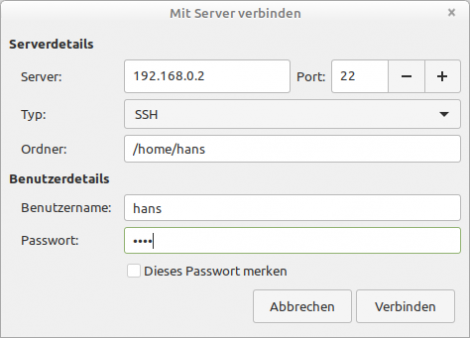
Figure 24.14.12.1: Dialogue - Connect to Server
After the successful connection, you will see the (remote) home directory mounted via the network in the file manager. Now you can safely copy files alternately. After copying, unmount the remote data carrier or bookmark this SSH connection.
24.14.13 Extension - X11 forwarding
An SSH server not only provides a console on the remote computer, but also the graphical user interface via the console of started programmes. Display redirection or X11 forwarding is handled by the SSH server if it has been configured accordingly. In the configuration file /etc/ssh/sshd_config, X11 forwarding must be allowed by the following line:
X11Forwarding yes
After changing the configuration file, the SSH server must be restarted:
honsek@laptop-mint20:~$ ssh hans@192.168.0.2 Last login: Tue Nov 30 17:56:50 2021 from 192.168.0.3 hans@pc-mint20:~$ sudo nano /etc/ssh/sshd_config [sudo] Passwort für hans: hans@pc-mint20:~$ sudo service ssh restart hans@pc-mint20:~$ exit
Decisive for the activation of display forwarding is the specification of the parameter -X when establishing the connection. You could then, for example, start the Gambas IDE on the remote computer and programme there remotely. However, you will see the Gambas window seamlessly on your local desktop.
honsek@laptop-mint20:~$ ssh -X 192.168.0.2 hans@192.168.0.2's password: Last login: Thu Nov 25 18:41:52 2021 from 192.168.0.3 hans@pc-mint20:~$ gambas3 hans@pc-mint20:~$ xed hans@pc-mint20:~$ thunderbird hans@pc-mint20:~$ beaver # Datenbank-Manager hans@pc-mint20:~$ exit Abgemeldet Connection to 192.168.0.2 closed. honsek@laptop-mint20:~$
As you can see, other programmes have also been launched on the remote computer that are known to be installed there. Note, however, that this form of connection does not support sound signals.

